Anonymizer chameleon open any blocked one. Tor browser - what it is and how Tor allows you to hide your online activities
Hello, dear readers of the blog site. You probably know that any of your actions on the network (website pages viewed, files downloaded, videos watched) can be tracked, and from completely different places (by contacting your Internet provider, rummaging through your computer, or searching in the logs of the sites you visited ). Anonymity on the Internet exists only if you don’t start “digging deep.”
There are some solutions to the “leaving trace problem” that we have already covered. For example, you can and then no traces of your visits will be saved on your computer. Or, for example, when blocking access to some sites (for example, to log into Contact or Odnoklassniki from a work computer).
But there is a much more comprehensive solution - this is the so-called TOR. Essentially this is software, which with a very high degree of probability allows you to hide from prying eyes everything you do and have done on the Internet. It’s precisely on the basis of this technology that it works Tor Browser, which will be discussed today. In essence, it puts complex technology into the shell of a normal-looking browser, accessible to any Internet user, which everyone can use. But its filling is unusual...
What is TOR?
I don’t want to overload you with technical terms and concepts that, by and large, will be superfluous. I’ll just literally outline in a nutshell (on my fingers) the principle of operation of the Tor technology and the Tor Browser built on its basis. This knowledge will allow you to understand what to expect from this software, what strengths and weaknesses it has, so that you can consciously use it for your needs.
So, initially all this was brewed in one of the US military departments. Why they needed it, history is silent, but at the beginning of the 2000s, the beginnings of Thor technology were completely unexpectedly laid out in general access. And they were open source codes and this software became freely distributed. What does it mean? And how much can you trust such a “gift”?
The question is fair, but you can trust it precisely because the code of this technology is open. The fact is that since then (over a decade and a half) these program codes have been studied (and made changes) by hundreds, if not thousands of people who understand this, and no “bookmarks” or “secret doors” have been found. Where it's about safety(in our case, transfer and storage of information), it is better to work with open source software (software).
By the way, this is why when choosing n, but for . They simply belong to the category of free software and their code has been checked by thousands of competent specialists. It’s somehow calmer, because I store a lot of passwords for services tied to money and losing them would be very expensive.
So, TOP technology allows you to access websites and download something from the network without leaving any traces behind. That is, when you open, for example, a website through the Tor Browser, it will be impossible to track the IP address of your computer on this website (and therefore to identify you). Even your Internet provider will not understand (even if you want) that you visited this site (and it will be impossible to prove it). Well, the browser itself will not store all traces of your wanderings on the Internet.
Wonderful, isn't it? I understand that in this way people can cover up their dark affairs. Not without this, of course. But the general idea of Thor is still bright - to provide the Internet user with real freedom in the form of complete anonymity. For example, in some countries access to certain resources may be blocked without justification, but Tor Browser will allow you to bypass these obstacles and not be punished for this violation, because they will not know that you did it (or they will not prove it). But that's not the point...
How TOR works? This is called onion routing. Look. There is a network of nodes owned by adherents of this technology. Three arbitrary nodes are used to transmit data. But which ones? And this is precisely what no one knows.
The Tor browser sends a packet to the first node, and it contains the encrypted address of the second node. The first node knows the key for the encryption and, having learned the address of the second, forwards the packet there (it’s like removing the first layer of an onion). The second node, having received the packet, has a key to decrypt the address of the third node (another layer has been removed from the onion). Thus, from the outside it is not possible to understand which site you ended up opening in your Tor Browser window.
But please note that only the path is encrypted(routing), and the contents of the packets themselves are not encrypted. Therefore, to transmit secret data, it would be better to first encrypt it (at least in the TruCrypt mentioned above), since the possibility of intercepting it (for example, using sniffers) exists.
In addition, this technology there are a few more disadvantages(or features):
- Your ISP (or anyone else who monitors your traffic) may realize that you are using Tor. He won't know what you're watching or doing online, but sometimes the mere fact of knowing you're hiding something can have consequences. Take this into account and, if possible, study ways to enhance camouflage (and they exist), if this is critical for you.
- The TOR network does not use special high-speed equipment, but, in fact, ordinary computers. This brings up another drawback - speed the transmission of information in this secret network can vary significantly and sometimes it is clearly not enough for, for example, viewing media content.
Where can I download the official Russian version of Tor Browser?
On this blog I have already published an article on that. There was also mention of the Torah. Naturally, it is better and safer to download any product from the developers’ website, i.e. the official one (I think you know). The Tor Browser download page is located at this address (I repeat once again that for security reasons it is better to download from the official website):
Please note that before clicking on the download button, you must select a language. The default is English, but you can select a dozen more options from the drop-down list, including fully localized Russian version. This is how it will work more pleasantly when the interface language is native.

Although, during installation you will again be asked about your preferred interface language and you can also select Russian there. Otherwise, the installation process is no different from installing any other browser.
However, when you first start you will be asked if you need to additional settings to connect to the TOR network. In the vast majority of cases, it will be enough to simply click on the “Connect” button:

It will take some time for the browser to successfully connect to the Tor network:

After this, a window will open in a browser that looks normal at first glance, but works with the Internet by creating encrypted tunnels (analogues).

However, the developers themselves emphasize that Thor is not a panacea(at least with default settings). Therefore, those who are paranoid about absolute anonymity are advised to follow the link for clarification on this matter.
How to use the Tor browser?
When you first load the browser, you are immediately prompted use anonymizer to search at disconnect.me. Actually, it is this service that will be used as “ ” in this browser (you can change this in the settings), i.e. when entering a request in newly opened browser tabs or when entering it through the address bar in any tab, the disconnect.me anonymizer will open with search results.
The search is actually carried out by Google (you can select from the settings in the top panel of the service - see the screenshot below), but no traces of who exactly conducted the search remain (remember, I wrote about the fact that, but in fact, nothing can be permanently deleted , so those who are concerned about anonymity need to remember this).

Don't forget also select search language(in the top panel of the disconnect.me window on the right), because thanks to the anonymizer, Google will not be able to recognize your preferred language automatically. Although, by choosing, for example, Russian, you to some extent lift the veil of secrecy about your incognito for this search engine. But here you need to make a compromise - either convenience, .
Yes, the Tor browser will also warn you when you first click on the link that it is better to load pages in English, to avoid, so to speak.

Personally, I chose the “No” option, because convenience is more important to me, and I don’t speak any other languages besides Russian. Alas and ah.
By the way, you can check it yourself that you have indeed been “encrypted”. To do this, it will be enough to go to the site from any other browser, and then do the same from under Thor. As you can see, TOR replaces (I became a sultry Norwegian) and this is only a small part of protecting your anonymity.

By the way, if you click on the onion to the left of the address bar, you will be able to see the same chain of three nodes (proxy) that separates your computer from the site you are visiting (I wrote about onion routing just above):

If desired, this chain of nodes can be changed. You can also change your “browser-created personality” if you don’t like the current one. However, this will close all open tabs in Tor and it will be automatically reloaded.
Here you can also access security settings:

By default, all privacy settings (anonymity are enabled), but the security level is at the lowest level due to the fact that only in this case you all functions of this browser will be available. If you set the security settings of the Tor browser to “high”, a whole bunch of browser functions will be available only after you force them to be activated (i.e., everything is disabled by default). For me this is overkill, so I left everything as it was, but you can choose something in the middle (compromise).
Otherwise Tor Browser is similar to Mozilla Firefox , because it is essentially assembled on its basis. This will be clearly visible when you go to settings (by clicking on the button with three horizontal lines in the upper right corner):

Good luck to you! See you soon on the pages of the blog site
You might be interested
 Incognito - what is it and how to enable incognito mode in Yandex browser and Google Chrome
Incognito - what is it and how to enable incognito mode in Yandex browser and Google Chrome  Search and browsing history in Yandex - how to open and view it, and, if necessary, clear or delete it How to do home page Yandex or Google home page, as well as any page (for example, this) set as home
Search and browsing history in Yandex - how to open and view it, and, if necessary, clear or delete it How to do home page Yandex or Google home page, as well as any page (for example, this) set as home  How to install WhatsApp on a computer - PC version and use WhatsApp Web online (via a web browser) How to install Google Chrome, Yandex Browser, Opera, Mazila and Internet Explorer on your computer for free
How to install WhatsApp on a computer - PC version and use WhatsApp Web online (via a web browser) How to install Google Chrome, Yandex Browser, Opera, Mazila and Internet Explorer on your computer for free
Anonymizer - what is it? The answer to this question interests many people, especially those who work in offices. Traveling across the Internet, we visit all kinds of resources - social networks, forums, game portals, thematic blogs. Not every user knows that information about him is stored not only on his device, but also on the sites he visits.
Of course, as a rule, there is nothing wrong with this, since the data is used, for example, to select news according to your region of residence or for other safe purposes. However, sometimes there are reasons why a “user” needs to log into a site anonymously, but not everyone knows how to do this.
After reading this article, you will learn how to “hide” on the Internet and receive information about some resources that provide this opportunity.
Anonymizer - what is it?
If you cannot access a website because you have been banned from it, then you have the opportunity to do this using an anonymizer. Maybe you just don’t want information about you to remain on some resource? In this case, for example, Cameleo will also help you - an anonymizer, or rather, a proxy server.

There are programs that need to be installed on your computer, as well as special sites (proxy servers). It is worth noting that you can use both paid applications or web servers and free ones.
By the way, the second option does not mean that the quality will be worse. Sometimes it's better to choose free option programs, as fraud is rampant on the Internet, which means you can download malicious software onto your computer.
For example, you have the opportunity to evaluate the free anonymizer "Chameleon". “Open any” is the motto of the utility, and indeed, you can do this with its help in just a few seconds.
Why are anonymizers needed?
In fact, the reasons for using such programs or resources can be completely different. Here are the most common:
- You work in an office, and your boss has banned you from using social networks and other entertainment portals. As a result, such sites are inaccessible to you (blocked). Of course, your boss is completely right, but if you think that you are doing quality work and you have time for social networks, then there is a way out - find the Chameleon anonymizer, open any blocked resource and kill time.
- Another reason is that you want to watch a movie on some portal, but a message appears warning that playing this video is prohibited in your region. To solve the problem, run an anonymizer or use a proxy server.
And these are not all the reasons. For example, if you change your IP address frequently, the chances of successful hacker attack your computer are significantly reduced.
Negative aspects of use
So, you have decided to actively use an anonymizer. Logging into almost any site with its help is carried out without problems. But here it is important to know that there is also a flip side to the coin.

What exactly negative aspects can arise as a result of the use of anonymizers? Here are some cons:
- The loading speed of site pages is usually much lower than without using an anonymizer. Especially it concerns free programs and proxy servers.
- You will not have access to all the features of the site you are visiting (for example, voting). In addition, if you use an anonymizer, logging into the site will require you to enter your username and password.
- By visiting proxy servers or installing programs, you put your computer at risk. A virus can penetrate it. Of course, there are anonymizers that have proven themselves well and can be trusted.
How to choose?
You don't want information about you to remain on the sites you visit, so you decided to use an anonymizer. You already know what it is, but you are wondering which proxy server or program to choose.
Here you need to follow several rules. Firstly, choose only proven anonymizers. Let it be free, but with a good reputation, because you provide such a service with your confidential data (logins and passwords from Email, social networks, other resources).
Secondly, if you need an anonymizer only for logging into, for example, the VKontakte website, then choose a proxy server specifically focused on social networks.
Thirdly, in order not to worry about the safety of your passwords, it is recommended to use paid programs and sites.
Cameleo - anonymizer for everyone
Of course, one of the best free proxy servers today is Chameleon. You don't have to spend money to use it. The site has an excellent reputation, so it is recommended to pay attention to it.

The interface is clear even to a schoolchild. After reading a few lines to get general information about the operation of the resource, you will immediately understand that you just need to insert the link of the web page you want to enter anonymously into a special field and click the “Go” button.
Now, even if you are banned from any site, you can easily access it.
Conclusion
So, after reading this article, you can safely use an anonymizer to log into various web resources (where you were blocked). You already know what it is, so all that remains is to choose the appropriate option.
Social networks have become an integral part of the life of modern people. For some it is a work tool, for others it is a source of news, for others it is a way to escape and relax. Therefore, when you cannot access the VKontakte website, you have to look for various options to solve this problem. The most reliable of them is to use the Chameleon anonymizer.
Reasons for restricting access
When they can’t log into the VK website, the first thing users do is start blaming the developers. Yes, failures in the operation of a social network do happen. But this is such a rare phenomenon that it is rarely encountered. Therefore, the source of the problem should be looked elsewhere.
Reasons for restricting access:
- account blocking due to violation of social network rules;
- restricting access within a certain region;
- established ban on entering social networks by the employer;
- Internet service provider failures.
Most often, users are looking for a “workaround” to visit social networks at work. To do this, they need to hide their IP address using an anonymizer. There are an endless number of them on the Internet, but today the most popular and stable is the Chameleon anonymizer.

"Chameleon" - what is it
Chameleon is an online service that makes it possible to hide data about the user’s location, equipment, web browser and other confidential information. With its help, you can visit any sites that are restricted for some reason. external reasons. Compared to other similar services, Chameleon has a number of advantages:
- high access speed;
- a large number of servers through which you can open blocked sites;
- no advertising;
- free access to service capabilities without registration and SMS;
- works online, there is no need to download third-party programs;
- convenience and ease of use.
If we omit complex technical terms, the operating principle of the anonymizer is as follows: the user enters the site URL into the address bar, and the service downloads it and creates a mirror on its behalf. After that, he opens the site, but at a different address.
To understand how this happens, let's move on to practice.
How to log into VK through Chameleon
You can use the service from any device that has Internet access. The main thing is to strictly follow step by step instructions presented below.
Step-by-step instruction:
- Go to the website http://cameleo.xyz/ through any Internet browser.

Sometimes providers may block this site. Therefore, when loading it, a “Page not found” error may appear.

- Next, you need to enter the address “vk.com” in the address bar or select it from the list below it.

- To go to the social network site, all you have to do is click the “Go” button.

- After this, the user is redirected to the VKontakte main page. Please note the change in the site address in the address bar before the “Welcome” inscription.

- To log into your account, you need to enter your login and password in the appropriate fields.

- The last step is to click the “Login” button.

It is worth noting that you can change your IP address through the anonymizer and go to mobile app VKontakte will not work. Chameleon can only be used within a mobile or desktop web browser.
To secure new information and consider everything in more detail using a live example, we suggest watching the video.
Let's sum it up
In the material presented, it turned out that in order to bypass the ban on entering VK, you need to change your IP address. Moreover, this rule applies not only to social networks, but also to news, entertainment and other web resources. Therefore, the presented instructions are universal and will come in handy for viewing more than once. limited content. If you have any questions about working with the service, leave them in the comments.
What, and now you can’t log into your social network account? Then an anonymizer for VKontakte (Odnoklassniki and other social networks) will help you. Let's figure out what it is.
It's no secret that most people visit social networks from computers at work. Those. Instead of working and benefiting our employer, we communicate on VKontakte and classmates, look for music, videos, etc. there.
Of course, this state of affairs does not suit our boss and he resorts to various measures to block our access to social networks.
Usually, the system administrator is simply given a command to close access to social networks from all PCs. The system administrator adds these sites to the list of prohibited sites and thereby blocks our access.
There is a solution - an anonymizer
There is a way out of this situation - an anonymizer that will allow us to secretly visit any sites.
What is an anonymizer? It is a specialized tool that hides data about the user and his PC on the Internet.
Such a tool can be a specialized software product or a special Internet site.
In most cases regular users use exactly these sites. Because they are very easy to use and widespread.
Such sites are called proxy servers. Proxy servers, also known as anonymizers, work as intermediary sites.
You just need to go to one of these anonymizers and enter your VKontakte address. And the proxy will redirect you there, but incognito for your system administrator.
The big advantage of proxies is that most of them are free.
Harmful system administrators
I wrote above that you will visit your favorite Vkontatka incognito, and the admin will not know anything. In fact, I was lying, admins are not fools either, and it’s not in vain that they get paid.
Sooner or later he will discover that you are using an anonymizer and will block him too. What to do?
Yes, everything is simple, as I wrote above, there are a large number of such sites. When one suddenly stops working, you just need to switch to another and that’s it.
Chameleon is one of the most popular anonymizers for VKontakte and Odnoklassniki. It is well known for its unique ability to disguise your Internet activities.
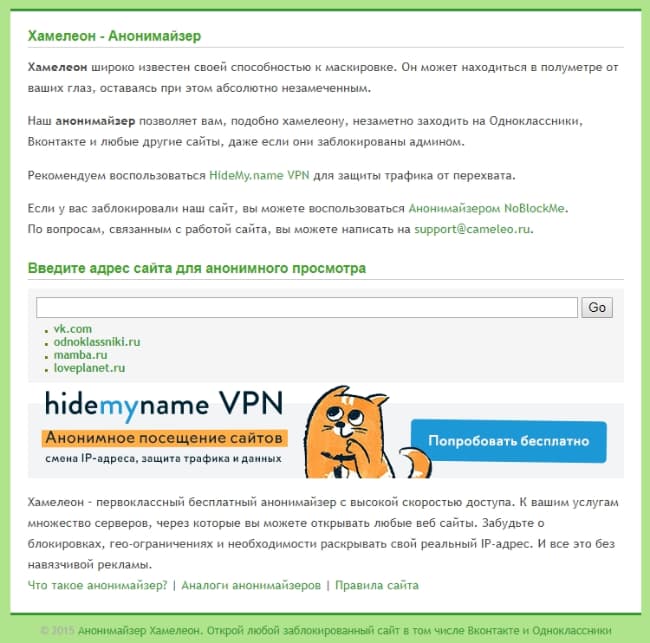
Moreover, it is completely free. So enjoy it for your health. It is available at cameleo.xyz
Also, for completeness of information, I bring to your attention a list of free anonymizers known to me.
cameleo.xyz - Chameleon - a free anonymizer for VKontakte.
daidostup.ru is a free proxy server for VKontakte.
katruk.ru/2 is another free anonymizer for the VKontakte website.
serqus.ru/2 - you can bypass the blocking of the VKontakte site through this anonymizer for free.
berock.ru/2 - a free anonymizer for full use of a contact if you are blocked.
raders.ru/2 - anonymizer for any sites.
razard.ru/2 - another Proxy Server
zerfod.ru/2 - free anonymizer in VKontakte.
gredor.ru/2 - a good anonymizer vkontakte.ru for free.
arkhaim.ru/ - free access to a blocked contact (vkontakte.ru).
vesvrabote.ru - 17 days of free use
v.antiblock.ru/ - anti-blocking for contact.
Sometimes employers block access to certain sites for their employees. In addition, in some countries, such as China and North Korea, website blocking is carried out at the country-wide level. In such situations, dissatisfied users who want to get to their favorite blocked site use various methods to bypass the block.
In the first part of this article I will tell you about all the ways to bypass site blocking, and in the second, we will talk about one interesting, in my opinion, way to open any blocked site and do it quickly, without installation special programs and without using Proxy and any anonymizers.
How to open any blocked site?
- Preface.
- Popular ways to open a blocked site.
- A way to open any blocked site without VPN, Tor and anonymizers.
The most common method is . Online anonymizers allow you to quickly and without installation additional programs on your computer to gain access to a blocked online resource.
But such sites also have their disadvantages. For example, if classmates or VKontakte are blocked in your office, and you go to the anonymizer website and enter your data, then in this case no one can guarantee that online service will not intercept your login and password, which, as you understand, is not good. We wrote in detail about how passwords of proxy server users are caught in the article “”.
Well, we must not forget that sometimes the anonymizers themselves fall under sanctions. For example, the popular anonymizer Chameleon was recently blocked in our country by Roskomnadzor.
There is also VPN technology, with which you can also bypass the blocking or get to the site where you were blocked. You can find out more about what a VPN network is by using the site search. And if you already know what a VPN is, then I recommend looking at the services.
And of course the well-known Tor. Some people use Tor to bypass blocked sites, and of course it does a great job, but I think that for the sake of accessing a blocked site it’s somehow not very serious. Onion routing is more suitable for providing anonymity and deep web. Although recently there has been a lot of noise about the facts of de-anonymization of Tor users. But despite this correct setting and used correctly, Tor can still provide enough high level anonymity.
Bypassing site blocking using a translator
Yes, friends, online website translators can not only translate texts, but also be in a good way bypass site blocking. Here are some of the most popular online resources that can solve the problem of accessing a blocked site.
They work very simply. Go to the online translator. Enter the address of the required site and set the translation language to Russian (if you need Russian as an output). Click translate and after a few seconds the blocked site loads.
In essence, online translators are the same proxies, but with a better level of trust. You can trust your passwords to such sites. But again, not for everyone, but only for those that I will talk about in this article.
Keep in mind that in some cases blocked sites may not be displayed entirely correctly, but this in no way prevents you from fully working with them.
Online translators
The first site we will talk about is the popular Google translator. You don't need a doctorate to understand his work. As I said above, enter the site address in the left window, select the language in the right window and click the Translate button.
After which the site itself will load. As you can see, the spy software is a little warped. But everything is quite readable, and those who previously celebrated the birthday of their beloved cat will not notice the difference at all.

The next online translator from the domestic search engine Yandex. It works on the same principle. We go in, type in and get the result.
The latest service from Microsoft's search engine Bing. Everything with him is the same as in previous cases.

Now about which service is better. If the reason for blocking is the site itself. Those. blocked you, or rather, if you were banned by a site, then all services here are equally good. Each of the sites reviewed did an excellent job with this matter.
Yandex translator shows blocked sites better than anyone else, I mean the visual part of the site. But Yandex refused to display some blocked sites at the Roskomnadzor level at all. In my opinion, the Bing translator handled this best; it was able to open any blocked site. Well, almost anyone. And the great Google, according to my experiments, ended up somewhere in the middle.
Well, that seems to be all. If you liked the article, share it with your friends and subscribe to news in in social networks. By the way, today I looked at your assessments of our articles on VKontakte and Facebook. Thanks to everyone who cares to like it. This is very motivating to write new articles. Good luck to everyone, friends!




